Penetration testers must be aware before they start the web application engagement if there is a WAF in place as the results of their attacks can be affected. Follow PenTest Lab Enter your email address to follow this blog and receive notifications of new posts by email. In this article we will try to examine the methods and the tools that will allow us to detect a WAF. WAF — Session Expired. How Scotiabank security breach happened. This is an important process that must be done in every web application penetration test during the information gathering stage in order to ensure that the results from the attacks that will performed are accurate. Nmap also can be used for this purpose as it contains a script that can detect a web application firewall. 
| Uploader: | Kajora |
| Date Added: | 14 May 2012 |
| File Size: | 22.2 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 70593 |
| Price: | Free* [*Free Regsitration Required] |
Wawf00f PenTest Lab Enter your email address to follow this blog and receive notifications of new posts by email. In this article we examined some methods and tools for detection of web application firewalls. Fingerprint is the method used to gather information about the target as much possible. In this article we learned, how to detect web application firewalls.

Of course an implementation of a WAF on its own cannot resolve the security problems that a web application might have and proper modifications must be made in order many of the attacks to be able to identified and blocked.
Many companies now days are wafw000f their existing infrastructure to implement web application firewalls. In the below image Web application firewall is between the classic firewall and the web server.
A good indication is by checking the cookies because some web application firewalls add their own cookie in the communication between the client and the web server. Virustotal uploaded 11 Malware related to Lazarus Group.
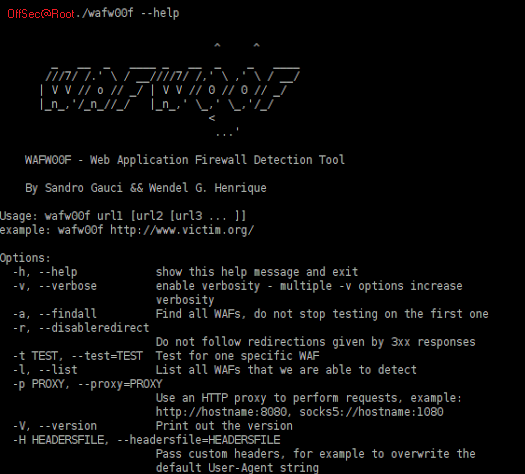
WAFW00F – Fingerprint & Identify Web Application Firewall (WAF) Products
However there are web application firewalls that can be installed directly into the web servers. WAF detection via Nmap. WAF — Network Topology. With this fingerprinting the pentester may develop an accurate attack scenario, which will find an vulnerability further, according waf0w0f ethical hacking.
How Scotiabank security breach happened.
Before starting you must know, where web application firewall is used over the network. This method is used initial phase of penetration testing. Penetration testers must be aware before they start the web application engagement if there is a WAF in place as the results of their attacks can be affected.
Specifically we run the script against the same website as above and the results were the following:.
Detect Web Application Firewall (WAF) before you attack
Confidential information of entrepreneurs and customers exposed due to unsecured networks. Waffw00f most common method for the pentesters is to fingerprint the target web presence.
Web application firewalls play an important role in the security of websites as they can mitigate risks and they can offer protection against a large-scale of vulnerabilities. The usage of this tool is very simple and can discover a variety of WAF products. Looking forward to it! The next image is showing the successful detection of a Citrix Netscaler firewall that protects the website. Most of the times a web application firewall is between a web server and a client like the one that we can see in the next image.
Finally there is a script that is capable only to detect Imperva WAF installations. Before knowing the web application firewall it is important to gather basic information of the target. By continuing to use this website, you agree to their use.
Detect Web Application Firewall (WAF) before you attack
Now we wil use basic telnet for fingerprinting a website. Web wacw00f firewalls cannot be resolve security problems on its own, proper configuration must be done to identify and block dafw00f external attacks, as per ethical hacking specialists. Detection of Imperva WAF. So if the penetration test is a white-box then this question should be asked in the initial meetings with the client.
Also by having the knowledge that a WAF is in place the penetration tester can try different techniques in order to bypass the protections and to exploit any weaknesses in the web application.
Detection of WAF with wafwoof. This site uses cookies.

No comments:
Post a Comment